Data Overload
Core Vulnerability Insight aggregates vulnerability data from every corner of your organization by collecting, managing and prioritizing raw network, web and client-side security assessment data. Disparate vulnerability data is consolidated across multiple locations and vendors, ultimately presented in a single dashboard.
With attack intelligence, Core Vulnerability Insight reveals how an attacker can traverse multiple vulnerabilities across layers of infrastructure and access your most valuable business assets. This attack simulation generates dynamic, multi-vector attack paths to critical business assets. These attack paths allow information security professionals to effectively narrow their focus on the most vulnerable points of their network, freeing up both information security and IT operations resources.
In recent deployments, Core Vulnerability Insight has demonstrated the ability to reduce tens of thousands of potential vulnerabilities from multiple scanners (types and vendors) by more than 70% to produce an actionable set of vulnerabilities based on consolidated data matched with known exploits
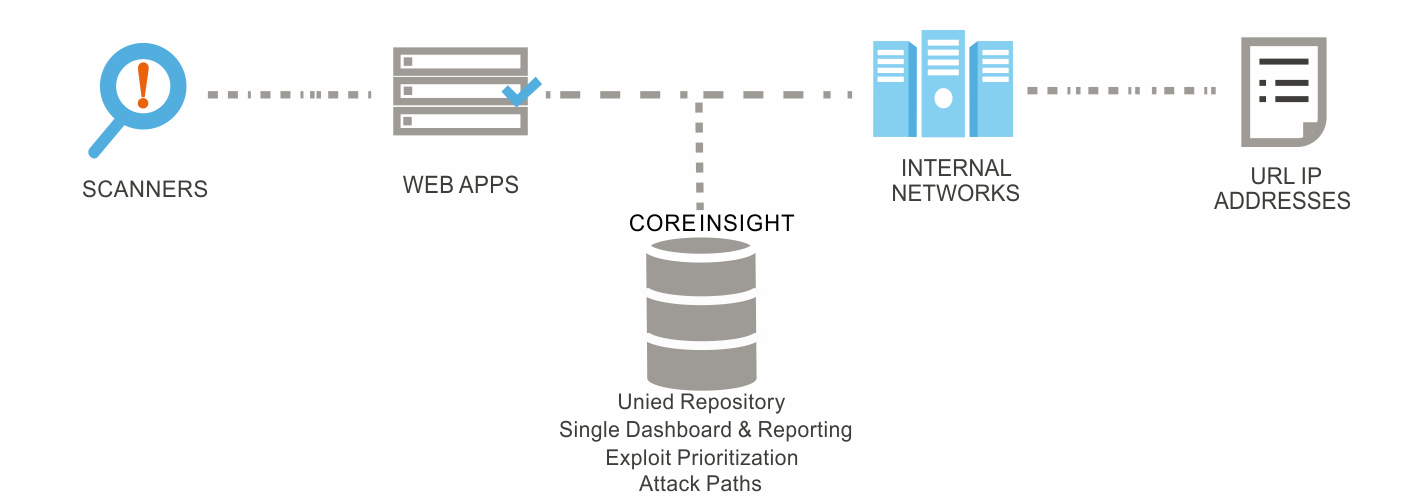
Core Vulnerability Insight gives you greater scalability and advanced attack path analytics helping you to accurately identify the vulnerabilities that pose the greatest threat to critical business assets, regardless of the size and complexity of your IT landscape.
Through attack path mapping, Core Vulnerability Insight reveals how adversaries can traverse multiple vulnerabilities across layers of infrastructure to reach and expose your most valuable business assets.
Single instance asset store for fast data import, analytics and queries
Pre-defined connectors to popular vulnerability assessment solutions
Demonstrate how attackers can chain vulnerabilities across vectors to move through your environment
Consider all possible exploits, including "in-the-wild", private, theoretical, wormified, virus and malware
Reveal specific assets and exposed resources
Validate systems and devices that may lead to critical business assets
Granular filtering, grouping and configuration of large amounts of data
Customize with templates and share